Once upon a time, doctors commonly visited sick patients in their homes. Although the practice has long since fallen out of favor, telemedicine creates a high-tech version of the house call by enabling real-time, two-way interactive video consultations between physicians and remote patients.
A natural gas compression plant was hit by a ransomware attack that forced it to shut down for two days, according to a Feb. 18, 2020, alert from the U.S. Department of Homeland Security (DHS). The attacker was able to access the plant’s IT network, and then move to its operational technology (OT) network. DHS’s Cybersecurity and Infrastructure Security Agency (CISA) said a lack of network segmentation allowed the attacker to cross the IT / OT boundary.
The increased use of digital technologies, cloud services and connected infrastructure has allowed oil and gas companies to increase efficiency and uptime, improve safety and reduce costs. However, it has also exposed the industry to heightened risk of cyberattacks.
Many of us have been the customer for a large project before. Perhaps for a home renovation. Perhaps for implementing a new system or installing new equipment at work. If these projects went well for you, you can probably recognize that the project manager made a significant effort to identify and manage your expectations. This led you to believe, throughout the life of the project, that things were under control. This eased your fears about the ultimate success of the project.
Every year, the Ponemon Institute puts out its Cost of a Data Breach Report. The latest edition shows that the cost of a breach has risen 12 percent over the past five years and now totals $3.92 million on average.
Firewalls are among the most important elements of network security, filtering traffic to allow the free flow of legitimate communications while preventing unauthorized access. However, rising management complexity is actually making firewalls a source of exposure.
Software-defined WAN (SD-WAN) continues to see strong adoption in organizations of all sizes. In a recent Frost & Sullivan survey, 15 percent of respondents said their organization has already deployed SD-WAN, and 18 percent said that deployment was currently under way. A whopping 61 percent said they plan to deploy SD-WAN within the next 12 to 24 months. That leaves just 6 percent with no plans to implement the technology.
There’s really no such thing as an 8 to 5 business anymore. Even if your office closes at 5:00 pm, employees still expect access to email, collaboration tools, and other applications and data. Customer-facing applications need to be available, too. And your cybersecurity tools better be working around the clock because hackers never sleep.
Technology drives business innovation and efficiency, but IT operations are not among the core competencies in most organizations. Managed services arrangements address this gap by providing access to advanced IT expertise while also helping organizations efficiently allocate limited resources and control spending.
Cybercriminals have healthcare organizations under siege, according to a new report from MalwareBytes. “Cybercrime Tactics and Techniques: The 2019 State of Healthcare” documents a stunning 60 percent increase in security threats in just the first nine months of 2019 compared to all of 2018.
In our last post, we discussed five of the top cyber security trends for 2020. Security analysts are predicting that phishing attacks will continue to increase, and that hackers will accelerate their use of AI-powered tools to automatically carry out attacks. Mobile devices will be targeted, as will data that’s stored in the public cloud without effective security controls. Analysts are also expecting an increase in “ripple effect” incidents in which multiple parties in a supply chain are attacked.
Cyber security is rapidly changing game of cat and mouse, with IT professionals attempting to stay one step ahead of increasingly sophisticated attackers. That’s why it’s important to keep abreast of emerging attack vectors and other issues impacting the security climate. Here’s a look at some of the future trends in cyber security that security analysts are predicting for 2020, and what organizations can do to reduce their risk.
In a previous post, we discussed the “last mile” connectivity problem — the limited performance associated with the shared Internet services available to remote offices and users. Most corporate data centers have a dedicated telecom circuit with guaranteed bandwidth and SLAs. However, it’s typically not cost-effective or even feasible to provision such circuits for remote locations.
In our last post we discussed the Patient Driven Groupings Model (PDGM), an overhaul of the way home health providers are paid by the Centers for Medicare and Medicaid Services (CMS). The new billing model creates hundreds of new categories for home health services, and implements a 30-day billing cycle to replace the current 60-day cycle. It also changes the way providers are assessed Low Utilization Payment Adjustments (LUPAs), and uses “behavioral assumptions” to identify providers that might structure services to maximize billing.
Last year, the Centers for Medicare and Medicaid Services (CMS) proposed a new billing model for home health services that would adjust payments based upon “behavioral assumptions” as opposed to actual provider billing or evidence of changes in billing behaviors. The Patient Driven Groupings Model (PDGM), slated to go into effect Jan. 1, is expected to reduce payments for home health services by 6.42 percent in 2020 alone — an estimated $1 billion.
Getting data from a data center to a remote user involves a complex system of WAN connections. A well-managed data center will likely have a high-performance connection to an Internet service provider’s (ISP’s) backbone with guaranteed bandwidth and SLAs. The data travels over the Internet backbone at high speeds.
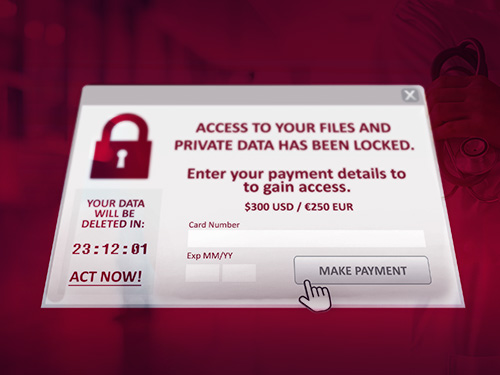
On September 20th, a ransomware attack forced a county health center in Wyoming to cancel surgeries, inpatient admissions, lab procedures, respiratory therapy, radiology exams and other services. Campbell County Health officials also reported that appointment schedules and medication orders were disrupted due to limited access to patient records and contact information. Although many services have been restored, the organization is still working to clean up its computer systems from that ransomware attack.
Quality patient care is the goal of every healthcare provider, but the reality is that many spend up to 60 percent of their time doing administrative tasks rather than delivering care. Doctors, nurses and administrators are all experiencing a time crunch due to steadily increasing management requirements.
On Jan. 29, 2015, health benefits provider Anthem, Inc. discovered that its IT systems had been hit with an advanced persistent threat (APT) designed to exfiltrate data. The cyber attack exposed the electronic protected health information (ePHI) of almost 79 million people, making it the largest healthcare data breach in history.
In previous posts we’ve been talking about cybersecurity in the marine industry. Malware could disrupt or disable the onboard systems in increasingly high-tech vessels. Far more likely are attacks targeting end-user devices that could result in costly IT system downtime or a data breach. In light of these risks, operators of maritime and inland marine vessels should implement a layered security approach that incorporates network and end-user security.
In a previous post on maritime cyber security, we reported on an official “Marine Safety Alert” issued by the U.S. Coast Guard in response to a cyber security incident involving a commercial vessel. The vessel’s onboard computer systems were infected with malware that “significantly degraded” their functionality. We discussed the maritime cyber security best practices recommended by the Coast Guard and the robust security tools GDS integrates into its marine connectivity solutions.
The oil and gas industry faces numerous challenges, including fluctuating prices, competition from alternative resources, geopolitical instability, and environmental and safety regulations. Companies in the energy sector must be as agile and efficient as possible to respond to changing demands, maximize market share and gain competitive advantages.
Professionals from all levels of the commercial marine transportation industry, from CEOs to deckhands, gathered in St. Louis last month for the Inland Marine Expo (IMX). IMX is the annual trade show for highlighting the latest equipment, services, trends and issues that are relevant to the transportation of goods along U.S. inland and intracoastal waterways. We at GDS were excited to be a part of IMX 2019.
On July 8, the U.S. Coast Guard issued an official “Marine Safety Alert” warning operators of commercial vessels of cybersecurity risks. The alert came in response to a February 2019 incident involving a vessel bound for the Port of New York and New Jersey.
Workers in the oil and gas industry often travel long distances to inspect and maintain pipelines and equipment. Tugboat and towboat operators are constantly moving up and down inland waterways. Construction management firms must send workers from job site to job site to oversee projects.
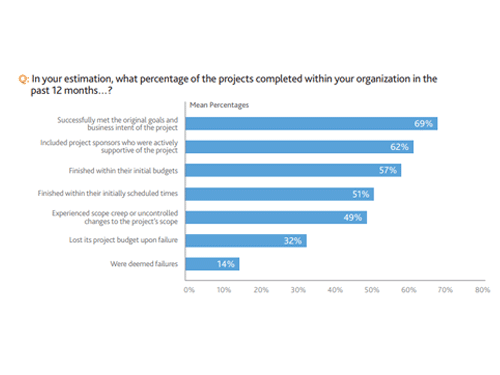
In a 2017 report from the Project Management Institute (PMI), 14 percent of all IT projects fail. However, this metric only tells part of the story. Of the projects that didn’t fail outright, 49% were late, 43% exceeded their initial budget, and 31% didn’t meet their goals.