On Jan. 29, 2015, health benefits provider Anthem, Inc. discovered that its IT systems had been hit with an advanced persistent threat (APT) designed to exfiltrate data. The cyber attack exposed the electronic protected health information (ePHI) of almost 79 million people, making it the largest healthcare data breach in history.
Managed IT Services Blog
Insights from GDS About Managed IT, Connectivity, Cyber Security & More
In previous posts we’ve been talking about cybersecurity in the marine industry. Malware could disrupt or disable the onboard systems in increasingly high-tech vessels. Far more likely are attacks targeting end-user devices that could result in costly IT system downtime or a data breach. In light of these risks, operators of maritime and inland marine vessels should implement a layered security approach that incorporates network and end-user security.
In a previous post on maritime cyber security, we reported on an official “Marine Safety Alert” issued by the U.S. Coast Guard in response to a cyber security incident involving a commercial vessel. The vessel’s onboard computer systems were infected with malware that “significantly degraded” their functionality. We discussed the maritime cyber security best practices recommended by the Coast Guard and the robust security tools GDS integrates into its marine connectivity solutions.
The oil and gas industry faces numerous challenges, including fluctuating prices, competition from alternative resources, geopolitical instability, and environmental and safety regulations. Companies in the energy sector must be as agile and efficient as possible to respond to changing demands, maximize market share and gain competitive advantages.
Professionals from all levels of the commercial marine transportation industry, from CEOs to deckhands, gathered in St. Louis last month for the Inland Marine Expo (IMX). IMX is the annual trade show for highlighting the latest equipment, services, trends and issues that are relevant to the transportation of goods along U.S. inland and intracoastal waterways. We at GDS were excited to be a part of IMX 2019.
On July 8, the U.S. Coast Guard issued an official “Marine Safety Alert” warning operators of commercial vessels of cybersecurity risks. The alert came in response to a February 2019 incident involving a vessel bound for the Port of New York and New Jersey.
Workers in the oil and gas industry often travel long distances to inspect and maintain pipelines and equipment. Tugboat and towboat operators are constantly moving up and down inland waterways. Construction management firms must send workers from job site to job site to oversee projects.
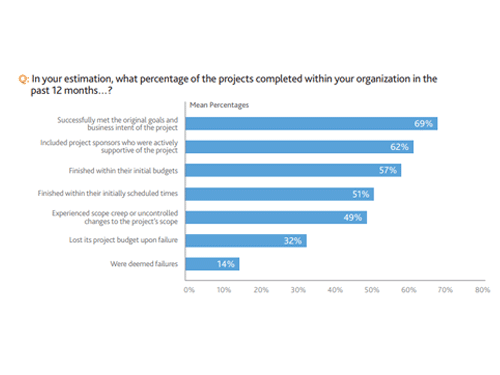
In a 2017 report from the Project Management Institute (PMI), 14 percent of all IT projects fail. However, this metric only tells part of the story. Of the projects that didn’t fail outright, 49% were late, 43% exceeded their initial budget, and 31% didn’t meet their goals.
The success of many organizations is largely dependent on the success of their branch locations. Satellite offices, retail stores, manufacturing facilities, distribution centers, and even vessels on inland waterways need IT resources to keep up with today’s business demands.
Not that long ago, the wide-area network (WAN) was used to connect a few branch locations to headquarters and headquarters to the public Internet. Today, the WAN has become the foundation of operations in a wide range of industries.
The cyber-threat landscape is always changing and evolving. Hackers are notoriously dynamic, constantly improving their tactics and tools to bypass the latest security countermeasures. Organizations that want to minimize their exposure to cyber threats need to be be well-informed and up to date.
As of July 20, 2018, tugboat and towboat operators must comply with new Coast Guard regulations designed to improve safety. Published in the Code of Federal Regulations at 46 CFR Subchapter M, the rules require that towing vessel operators submit to an annual Coast Guard inspection or implement an approved towing safety management system (TSMS). Many operators are deploying onboard vessel management systems to help meet these requirements, but are struggling to maintain the real-time data communications needed to make the management systems work properly and ensure compliance.
There’s a reason why more than 90 percent of targeted security threats originate in email. Human beings are the weakest link in the security chain. If an email gateway is like a brick wall that surrounds the network and only lets in a small percentage of threats, a human being is often like a turnstile that only requires a gentle push to gain entry.
Experts say that a security breach is virtually inevitable — that it’s a matter of “when” not “if.” However, rapid detection and response to a security incident can greatly reduce its impact, as GDS proved recently when it stopped a ransomware attack.
Earlier this year, an attack was carried out against IT service providers. This attack was so damaging that the Department of Homeland Security and FBI Cyber Unit issued high priority alerts. It was the kind of attack that IT providers dread...and it quickly revealed who among them was prepared and who was not.
Given that time and budgets are always limited, organizations are often reluctant to upgrade IT infrastructure that seems to be working just fine. If it ain’t broke, don’t fix it. But the fact that something appears to be working isn’t enough in today’s cyber threat climate.
According to the Center for Strategic and International Studies, cybercrime costs the U.S. economy about $100 billion each year. As soon as you think you have one threat properly defended, a new, more dangerous threat emerges. This is why organizations continue to make major investments in IT security, to prevent data breaches and minimize their impact and to satisfy increasingly complex regulatory compliance requirements.
Many in-house IT teams are struggling to keep up with day-to-day administration and management tasks. The IT environment has become increasingly complex, encompassing a broad range of on-premises and cloud-based platforms. Growing numbers of users are accessing these systems with an array of mobile devices. An ever-increasing volume of data must be stored, protected and backed up. Organizations are under constant attack by a never-ending barrage of security threats.
There is no organization on the face of the earth, regardless of how sophisticated its security defenses may be, that is immune to a data breach.
IT systems should create value for your organization, drive operational efficiencies and support growth. Given the constantly evolving nature of technology, those objectives are always going to be moving targets. That’s why organizations should regularly engage in strategic IT planning to identify how technology assets are currently performing and where future investments will produce the most benefit.
Changing traffic patterns and bandwidth requirements are forcing organizations to rethink their WAN architectures and data transport options. In the past, most applications and resources were hosted in the corporate data center, and branch locations connected to headquarters in a hub-and-spoke architecture. Today, the WAN primarily supports Internet traffic and cloud access, making traditional designs costly and inefficient.
There’s no way to guard against every cybersecurity threat. Some of the largest enterprises in the world, with skilled IT teams and large budgets, have fallen victim to massive security breaches. There are simply too many devices and applications to protect, with new threats emerging every single day.
In our last post [Software-Defined WAN: Cheaper, Faster, More Secure], we discussed how software-defined WAN (SD-WAN) solutions enable you to reduce WAN cost and complexity while increasing performance, reliability and security. The software-defined component of SD-WAN lies in a smart centralized controller capable of differentiating and segmenting traffic and making routing decisions on the fly.
The IT industry is often guilty of hype and oversimplification. New technologies are marketed in a way that creates overinflated expectations, while the potential challenges associated with implementing and managing the technology are minimized. Software-defined WAN (SD-WAN) technology has, for the most part, lived up to the hype.
Software-defined WAN (SD-WAN) technology is being adopted at a phenomenal rate. IDC expects that 70 percent of enterprises will implement some form of SD-WAN within the next two years. As a result, the research firm predicts that the SD-WAN market will see a compound annual growth rate of more than 90 percent.
We often have conversations about Cyber Security, even with those that are not focused on the protection of systems and data. So little is known or understood that people are often unaware of the threats around them. Most people just don’t see them. In a discussion regarding the compromise of a student records platform at a school, a general attitude of “So what if some student records are changed?” How bad can that be? If we consider that these individuals will become adults with a credit history, then we can see that this could be the origin of an Identity Theft exploit. The focus of this white paper is to shed some light onto a very dark topic – Cyber Security.
Get In Touch
310 Laser Lane
Lafayette, Louisiana 70507
Office Hours: Monday - Friday
8 a.m. - 5p.m.
Contact Us >
24 / 7 / 365 Support
Our dedicated support
staff are available by
phone 24 hours a day.
Phone: 888-435-7986