Healthcare Ransomware Attacks Require Preventive Care
On September 20th, a ransomware attack forced a county health center in Wyoming to cancel surgeries, inpatient admissions, lab procedures, respiratory therapy, radiology exams and other services. Campbell County Health officials also reported that appointment schedules and medication orders were disrupted due to limited access to patient records and contact information. Although many services have been restored, the organization is still working to clean up its computer systems from that ransomware attack.
It was one of at least 491 ransomware attacks this year that targeted U.S. healthcare providers, according to a new report on ransomware from Emsisoft. That represents nearly 80 percent of all ransomware attacks the company has identified through the first nine months of 2019.
Healthcare is the most-targeted industry in the U.S. for ransomware for several reasons.
As the second-largest sector of the U.S. economy, it is an enticing mark. It’s also the source of vast amounts of valuable personal, medical and insurance data. Furthermore, it has a reputation for notoriously inadequate security measures — a recent global survey by Gartner found that healthcare organizations spend about 5 percent of their IT budgets on security, last among 13 industries surveyed.
Gartner found that healthcare organizations spend about 5 percent of their IT budgets on security, last among 13 industries surveyed.
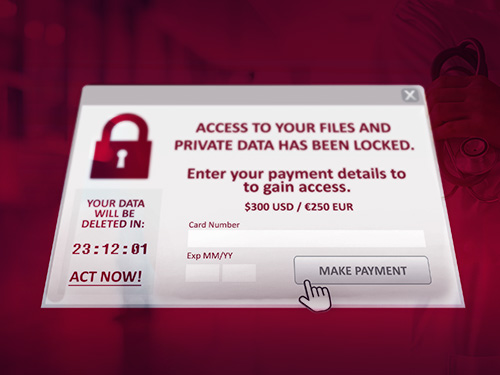
Most important from a ransomware perspective is that healthcare targets tend to be willing to pay up to regain access to their data. Unlike other industries that might lose revenue or customers due to an interruption, these attacks are literally life-and-death matters for healthcare organizations.
Unfortunately, paying the ransom to regain access to encrypted or otherwise inaccessible files doesn’t always work. In many cases, organizations that pay are never provided with decryption keys. Even if access is regained, the data may not be clean. In some cases, malware planted by hackers is activated months after the original ransomware attack.
Without question, robust backup practices provide the best defense against ransomware by ensuring you can reliably access essential resources in the event of an attack. Data should be backed up frequently to meet recovery point objectives and keep potential data loss to an acceptable level. Because restore time will often determine the true impact of a ransomware attack, recovery time objectives need to be established based on an acceptable period of downtime.
Key Precautions Your Healthcare Organization Can Take to Protect Against Ransomware
It’s important to remember, however, that ransomware attacks typically spread across the IT environment and can affect backup systems. Backups must be isolated to ensure malware can’t get to them, and the environment continually monitored to rapidly detect an attack.
Here are some other key precautions recommended by the HHS Healthcare Cybersecurity and Communications Integration Center:
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most ransomware attacks.
- Train users on how to detect potentially malicious software, and continually remind them they should never click on links or open attachments in unsolicited emails.
- Restrict users’ permissions to install and run software and apply the principle of “least privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its ability to spread through a network. Smart network access management is key.
- Use application whitelisting to allow only approved programs to run on a network.
- Enable strong spam filters to prevent phishing emails from reaching users and authenticate inbound email to prevent email spoofing.
- Scan all incoming and outgoing emails to detect cyber threats and filter executable files from reaching users.
- Configure firewalls to block access to known malicious IP addresses.
In the event of a successful cyberattack, infected computers should be isolated as soon as possible to protect networked and shared resources. All network passwords and online account passwords should also be changed as soon as possible.
Managed Security Service Providers Can Help Protect Your Data
Ransomware is flourishing because it’s an easy source of income for cybercriminals, and the threat will likely continue to grow over the near term. With well-designed backup operations and best-practice security measures, healthcare organizations can significantly reduce their risk. Contact GDS to discuss how our end-to-end, fully managed security services can minimize the impact of a ransomware attack.
Contact Global Data Systems Now >
Get In Touch
310 Laser Lane
Lafayette, Louisiana 70507
Office Hours: Monday - Friday
8 a.m. - 5p.m.
Contact Us >
24 / 7 / 365 Support
Our dedicated support
staff are available by
phone 24 hours a day.
Phone: 888-435-7986

